One of the dark sides of the Crypto market today is that it contains a lot of holes in the security stage, from which hackers have taken advantage of this lucrative “bait” and have performed many “games” to bypass investors. subjective and careless. Brief statistics have had many cases of fraud in the past and the value of lost assets amounted to hundreds of millions of dollars.
So, today Allinstation will take a look at some of the ways that hackers can steal money and show you some notes to take to avoid losing money!
Common types of scams
Malicious files

Malicious files are usually files containing malicious code that when we download or activate them, they can take control of our device, from which they will automatically use our computer to steal assets as well. as important information.
Malicious file extensions often have the form of .exe because the program can perform access rights when we have installed it. These files are often located in pirated software, or parts of unknown origin, cracked software. There is another type of malicious file that is saved as Rar or Zip. When we extract these files, the subfiles containing the malicious code are activated and the hack will perform bad actions on the infected device.
How to take precautions
Do not download pirated software, pirated documents because they often contain malicious files in them.
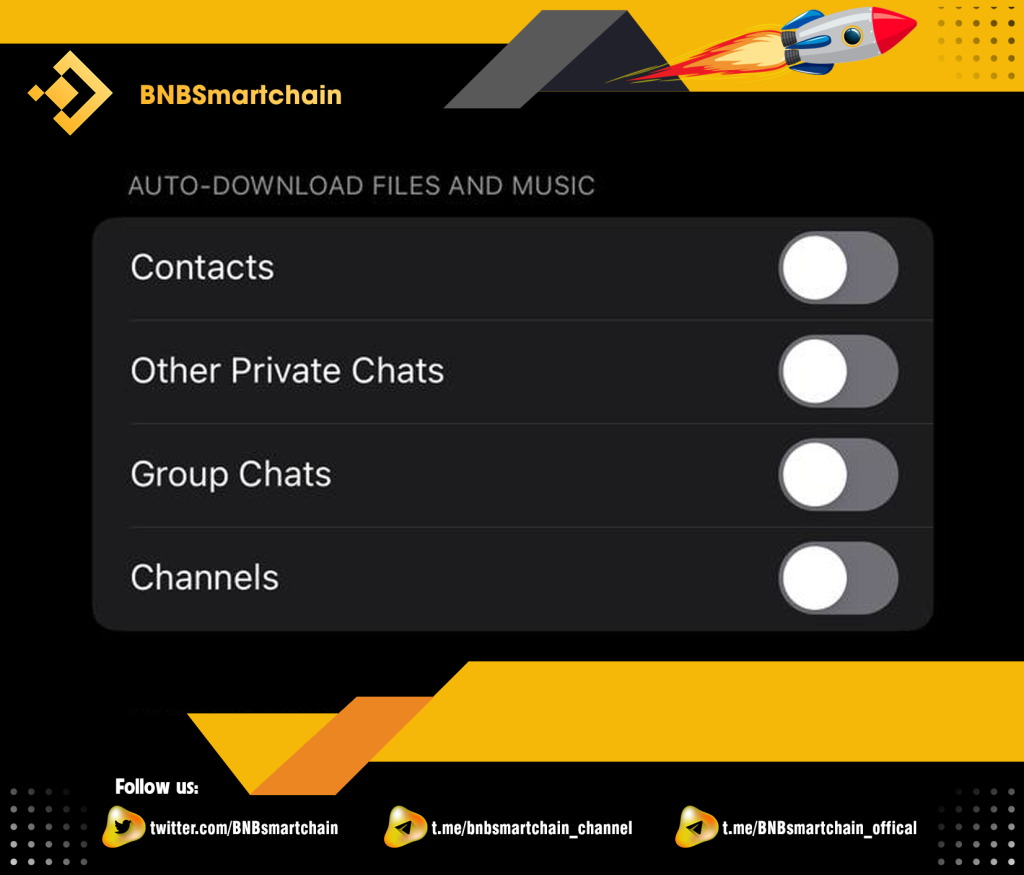
Many brothers use Telegram but do not pay attention to its automatic file download feature. It is this feature that makes your device more accessible to hackers. Please follow the instructions to turn this feature off!
Step 1: You select “Data and Storage” in the settings of the application.
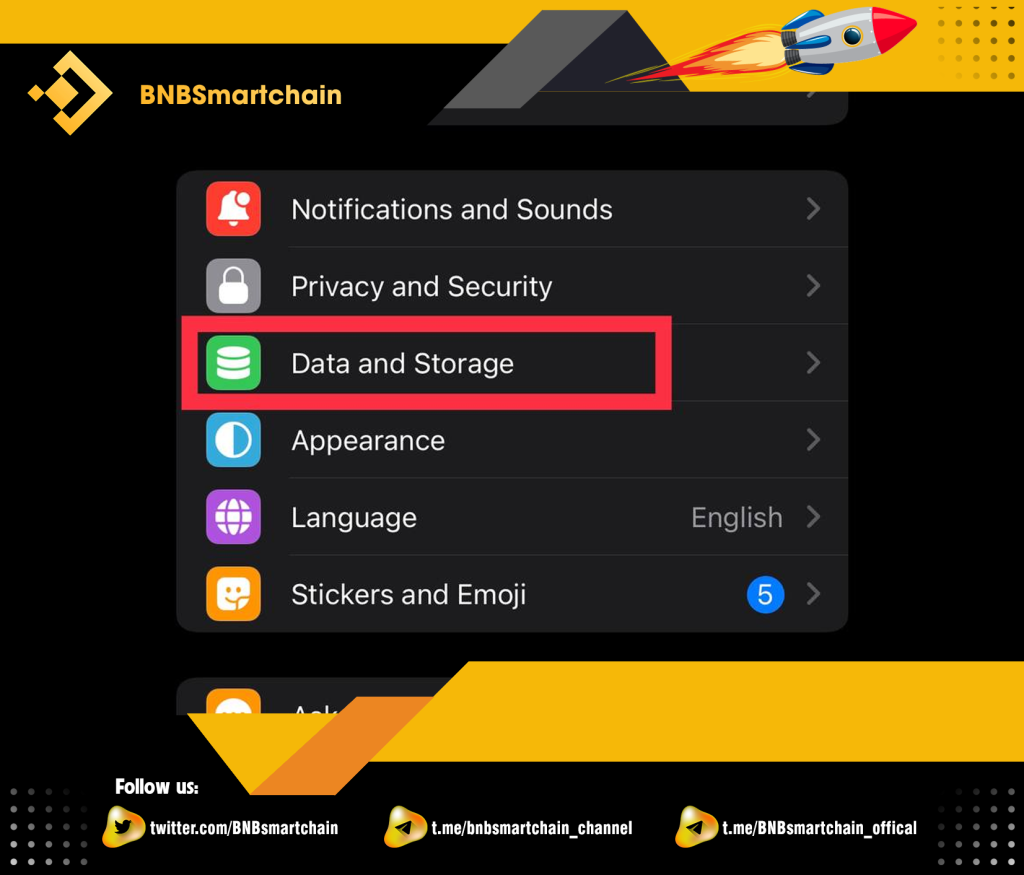
Step 2: You select both items as shown in the picture.
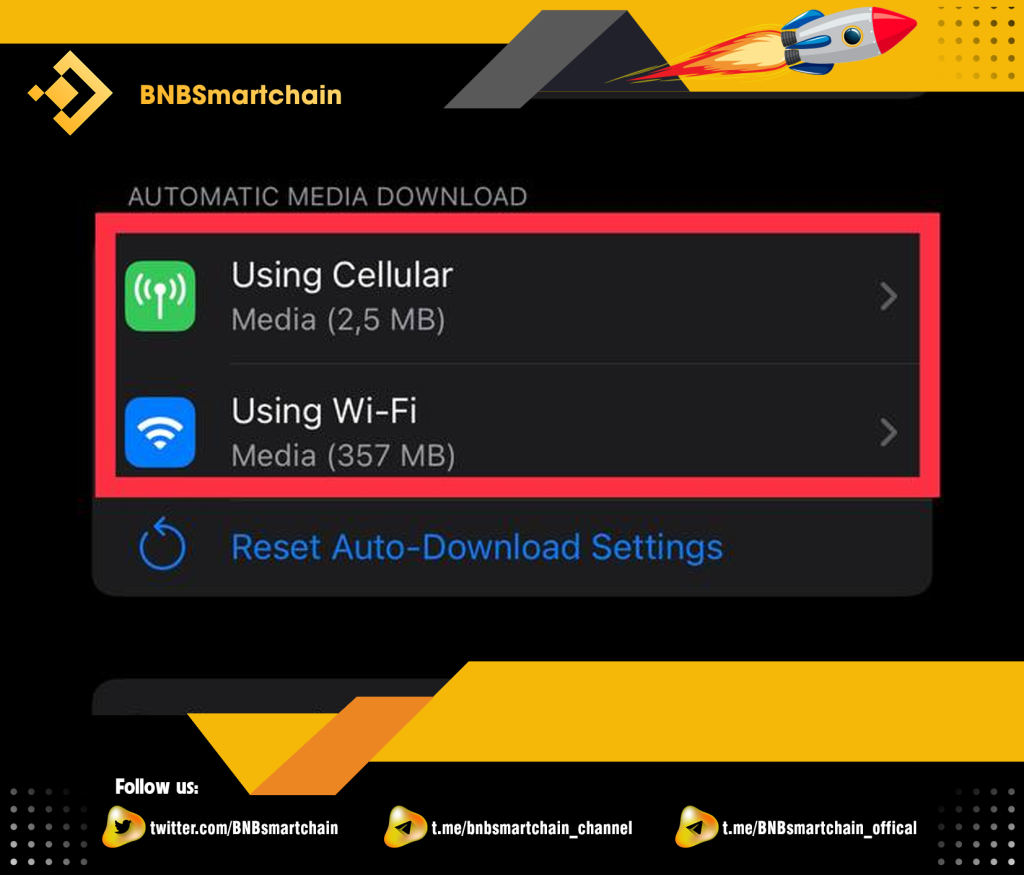
Step 3: Then you click “Files”
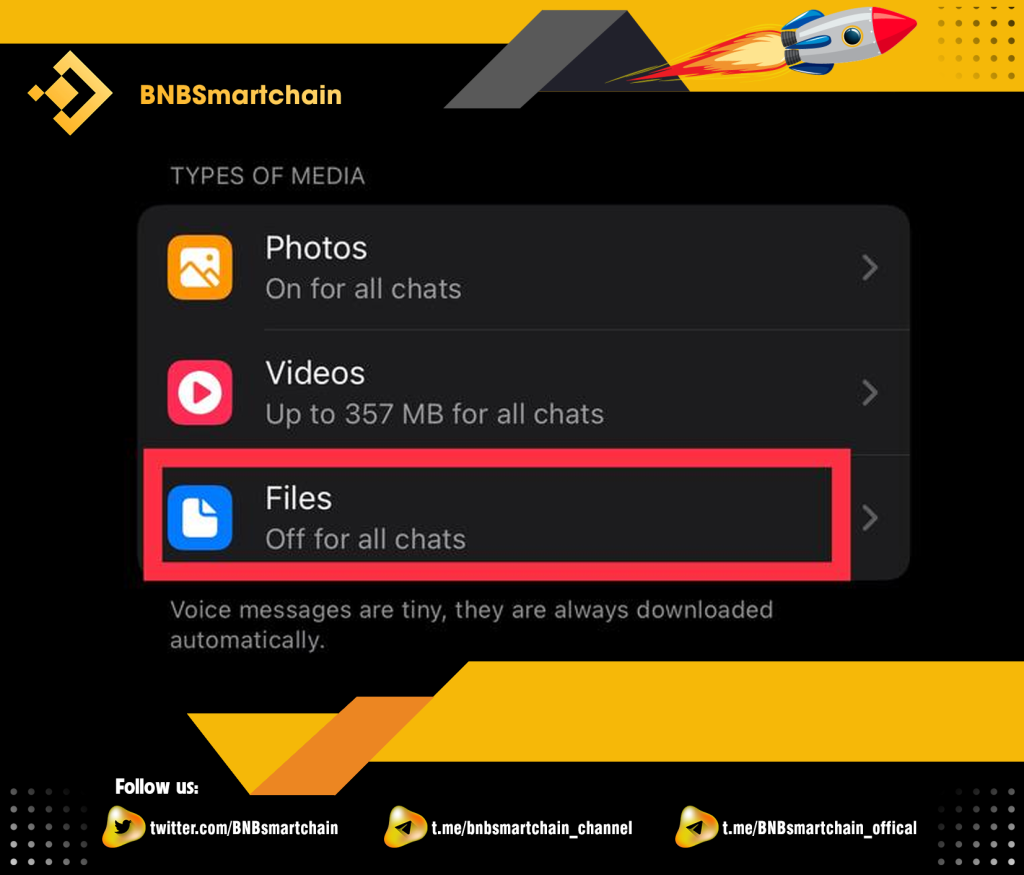
Step 4: Turn off the settings as shown in the picture. So you have turned off the automatic download function on Telegram already!
Các cá nhân/hội nhóm giả mạo

This form often appears on social networking platforms such as Facebook, Telegram, Twitter… Especially on Telegram because often investment groups will appear on Telegram quite a lot and this is also the favorite platform of scam groups. scam because it will be easy to trick you through impersonating the big KOLs in the market or the big communities in the market by:
Set bio and Username information similar to the big KOLs in the market
Example: Username Nguyenvana is real KOLs. The fake will set the username as Nguyenvanaa or Nguyennvana,… and let Bio be Nguyenvana (Because Bio we can fill in anything), with the purpose of fooling you.
I want to note to you one quite important thing that most of the big KOLs in the market will never actively message and ask you to transfer money for private investment or entrust as well as borrow money. money… So when you encounter the above cases, you’ve probably encountered scammers!
Added to fake groups
It is quite important that before you join a certain group, you should carefully check whether it is the official Group of that community because nowadays scammers are quite sophisticated, they will try to Try to build a professional group of scammers that look like official groups, so be careful!
Fake application of cryptocurrency exchanges

One popular fake app in spoofing exchanges is Poloniex, which was launched by hackers before the exchange announced its official exchange app. The purpose of the hacker is to get login information when the user enters the fake application.
To avoid unexpected situations and hackers to take all your money, before downloading, you need to check whether the platform has announced the application or not, whether you have downloaded the correct official application or not. One thing you need to do is two-factor authentication (2FA), so that when someone else has your account information, they still cannot log in.
Fake Cryptocurrency Wallet Apps
These applications aim to get your wallet password, 12 characters or private.
Or they can provide the hacker’s addresses instead of your wallet address, so that when you transfer assets from one wallet to another, the asset can be transferred to the Hacker’s wallet, not the wallet. of brothers.
How to take precautions
You need to carefully check cryptocurrency wallets before downloading and using them.
The private key and 12-character codes should not be saved on electronic devices, instead, you can write them down on paper or note them in places where you can’t connect to the Internet or want to save them online. On electronic devices, it is possible to swap positions of 12 characters or replace characters with synonyms and antonyms.
But note that you must remember the characters that you have replaced!
Hidden Cryptocurrency Mining Apps

Hackers are getting more sophisticated and are also planning to develop into integrated malicious programs that masquerade as video games, gadgets or even learning applications.
They even run ads for these applications with the aim of giving users great rewards for mining coins through their applications to beat the greed of users. It is worth mentioning that the rewards are sent through to the developer (Hacker) instead of returning to the user, They are even more sophisticated by implementing algorithms to be able to mine the cryptocurrency but it is very light and does not cause too much impact through the user experience to avoid detection.
When your electronic device is infected with these malicious codes, it will reduce performance, reduce device usage time and, importantly, cause damage to components more easily.
How to take precautions
- Always update to the latest versions of devices and applications.
- Only install official software, do not use pirated Crack version because in these applications, Hackers can easily install malicious files to allow cryptocurrency mining on the device. of brothers.
- Use web browsers that protect against malware such as MinerBlock, NoCoin and Adblock, or perhaps install anti-virus software and keep them updated.
- It should be remembered that mining cryptocurrencies requires specialized hardware (ASIC), which means that it can only be mined on computer devices with video cards with powerful GPUs, and currently, Coin mining by phone is almost impossible to exploit, if it can be exploited, the amount of money received will be very little.
Public Wifi Network

Often hackers will take advantage of our need to use the Internet, thereby creating public Wifi supplies with malicious code, when we connect to wifi, we have allowed criminals. criminals have access to the data on our devices. You should limit public Wifi hotspots to ensure your safety!
Clipper apps

This is a relatively dangerous case because this application changes your electronic money address only when pasting in the address box before sending. Sometimes the scam wallet address may be close to your wallet address in the first and last letters so that you cannot recognize it and thereby lead to sending assets to the hacker’s wallet.
To avoid this situation, you always have to double check the recipient’s address before the transaction. Crypto transactions once you have sent them cannot be canceled or refunded, so you need to check carefully to avoid losing money.
Phishing attack

Phishing Attack is a form of attack that steals user data. Phishing Attack is designed to impersonate a reputable individual with the purpose of tricking people into revealing or stealing personal information, banking data as well as important information such as card information. Banks, usernames, passwords of trading accounts… Sometimes let them deploy malicious software on the victim’s device like ransomware.
Prevention
- With emails of large corporations, you are not required to enter login information as well as personal information. You can call the operators of the companies to confirm before filling in any important information!
- Do not disclose personal information such as phone numbers, account numbers, and email addresses on the Internet because hackers can take advantage of this loophole to trick you.
- Do not click on any links with obscene content or links that require clicking to enter personal information. Do not respond to or confirm messages that are fraudulent, or steal information from fake organizations.
- Bookmark the addresses of financial-related websites that you often use on the toolbar of your web browser.
Summary
Through the above article, Allinstation has pointed out common forms of fraud on electronic devices in the Crypto market, along with instructions for you to avoid as well as know how to handle situations. How to avoid unexpected situations caused by Hackers. Hopefully the above article will help you protect your electronic devices as well as valuable digital assets!